Virtual CISO Services
vCISO Strategic Consulting With Operational Support
Virtual CISO Services – Your strategic cybersecurity partner
Mid-market companies are navigating an increasingly complex digital landscape, fraught with evolving cybersecurity challenges. Cyber Defense Group’s Virtual CISO services provide a comprehensive solution tailored to tackle cloud complexities, bridge in-house expertise gaps, combat emerging threats, and ensure regulatory compliance. With us, you gain a dedicated cybersecurity expert committed to protecting your business.

Benefits of our virtual CISO services
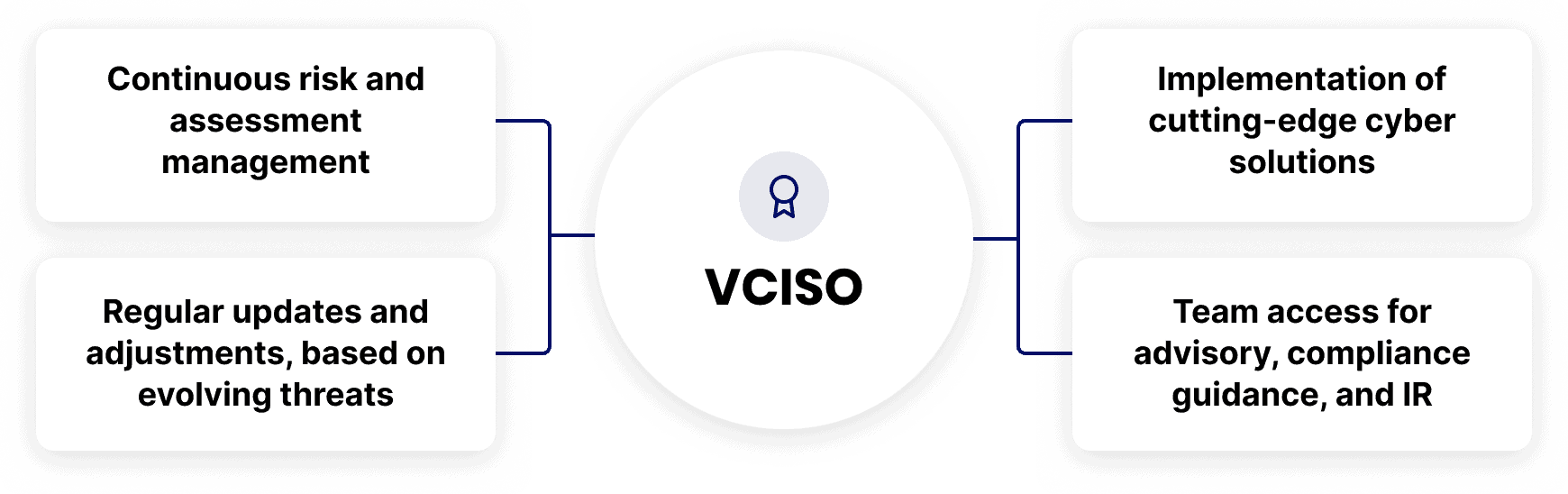
Our vCISO security experts seamlessly integrate with your teams, providing the expertise needed to fortify security posture, ensure compliance, and proactively manage cyber risk.
By taking a proactive approach to security, we ensure that potential threats are mitigated before they become issues.
Strategic cyber planning aligned with your business goals
Enhanced risk management and compliance posture
Cost-effective access to top-tier cyber expertise
Business outcomes you can trust
Embrace a future where your security program enables rapid innovation. With Cyber Defense Group’s vCISO services, your business will achieve:
ROI through enhanced cybersecurity resilience
Peace of mind with comprehensive compliance and risk management
Strategic advantage through cybersecurity excellence
How our services work
Our virtual CISO services will assess your security posture and develop a tailored strategy, leveraging frameworks like NIST and can align with various security regulations such as PCI, HIPAA, GDPR, and FINRA.
This hands-on approach ensures that your cybersecurity measures are not just reactive but proactively aligned with your business’s growth and innovation goals.
EditShare leverages Cyber Defense Group Virtual CISO services
EditShare provides shared storage and media management for smart workflows in media and entertainment.
EditShare partnered with Cyber Defense to strengthen security with a dedicated virtual CISO, addressing rising cyber threats in the media sector.

Why Choose Cyber Defense Group Virtual CISO services?
Strengthen your security with Cyber Defense Group’s Virtual CISO services, combining cybersecurity management with strategic business growth.
Partner with Cyber Defense Group to turn cybersecurity into a strategic asset, building a resilient digital environment for your business.
Bespoke security programs
Get vCISO support tailored to your business, ensuring security drives growth and innovation.
Proven expertise
Leverage our experts in retail, tech, healthcare, and fintech for insights on industry challenges and compliance.
Cost-effective leadership
Get executive insights without the cost of a full-time hire. Maximize your cybersecurity investment.
Agile and proactive approach
Stay ahead with defenses built for emerging threats and technologies.