What is Third Party Risk Management? A Comprehensive Guide

In the rapidly evolving digital landscape, where sophisticated threats abound, comprehending and mitigating third-party risks weigh heavily on the minds of risk managers. With 71% of organizations noting an increase in vendors within their third-party network compared to three years ago, understanding what is third party risk management has come to a critical head.
The Importance of Third Party Risk Management

Third party risk management (TPRM) involves the process of identifying, assessing, and mitigating risks associated with external or third-party vendors, suppliers, and service providers within your business’s supply chain. As businesses increasingly rely on these external partners to enhance efficiency and competitiveness, the potential for cybersecurity threats also grows. Recent third party data breaches have highlighted the need for effective TPRM to safeguard sensitive data, ensure regulatory compliance, and protect the integrity of business operations against the backdrop of sophisticated cyberattacks.
Third-party risk management within a comprehensive cybersecurity management program assesses all security aspects involved in outsourcing to third parties, encompassing risk criteria establishment and third party partner and vendor onboarding and screening. Let’s explore what is third party risk management!
What Does a Third Party Risk Assessment Include?
Third-party risk management is done through a third party risk assessment, also sometimes referred to as a vendor or supplier risk assessment. This is a comprehensive evaluation of potential risks associated with each vendor relationship a business has established. This assessment aims to identify and analyze possible security risks such as data security, operational efficiency, regulatory compliance, financial stability, and reputational impact.
The assessment typically includes the review of documentation like contracts, security policies, and compliance certifications, as well as conducting audits and interviews. The objective is to identify vulnerabilities susceptible to cyber threats or operational disruptions.
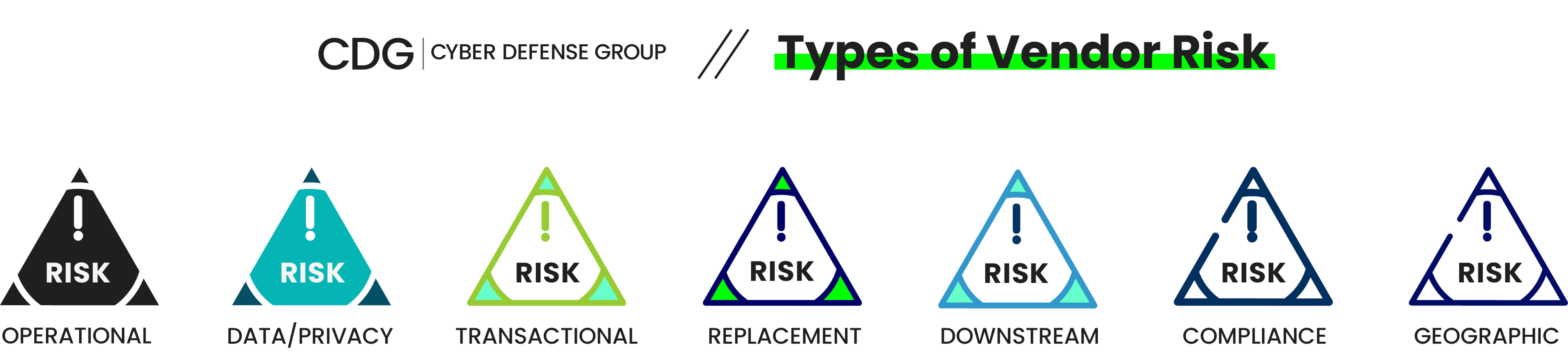
Key Third Party Vendor Risk Categories
- Operational Risk: Importance of the vendor’s services to core business functions.
- Data/Privacy Risk: Whether the vendor handles sensitive or regulated information.
- Transactional Risk: Involvement in financial transactions.
- Replacement Risk: Ease of replacing the vendor if services are disrupted.
- Downstream Risk: Use of subcontractors that may introduce additional vulnerabilities.
- Compliance Risk: Adherence to required industry regulations.
- Geographic Risk: Vendor location and geopolitical considerations.
Source: Security Magazine
How to Onboard and Screen Third Parties
Experts advise creating a formal structure for your third-party risk management program to standardize all third-party onboarding and screening. Leveraging AI-powered platforms in third-party management can improve the accuracy of risk assessments and identify vulnerabilities in the digital supply chain. Businesses should also take comprehensive real-time risk-checking and containment methods to ensure a thorough third-party risk assessment.
Using Technology to Strengthen TPRM Programs
Technology can significantly enhance the efficiency and accuracy of your TPRM efforts. Benefits include:
- Real-time monitoring of vendor risk across all third-party relationships.
- Data collection and macro-level analysis to inform future vendor decisions.
- Assessment of internal and external risks through automation.
- Continuous evaluation of risk metrics and third-party performance.
Building Your Incident Response Plan for Vendor Breaches
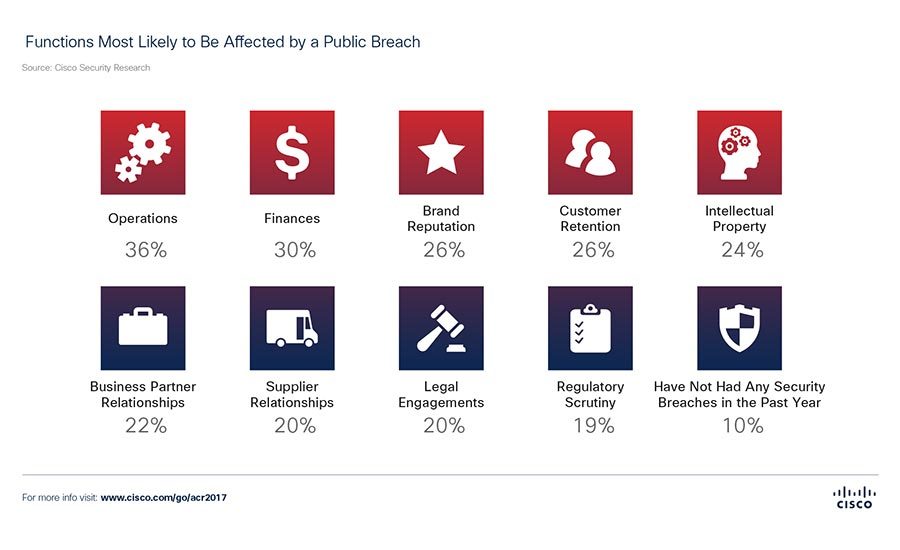
While many businesses have incident response plans in place, they often fall short in addressing third-party breaches. Consider the following:
- When and how should the vendor be notified?
- Who is the point of contact?
- What specific breach details should be shared?
- How will the breach be mitigated?
- What preventive steps will be implemented going forward?
How Often Should You Conduct TPRM Assessments?
Managing third-party risk is a dynamic challenge. Conduct regular assessments:
- Annually for existing vendors.
- Onboarding for all new third parties.
These assessments should include documentation management, compliance reviews, insurance validation, and network diagrams.
Use frameworks such as ISO 27001 or NIST to guide and structure your risk assessment processes.
Best Practices for Third-Party Risk in Cybersecurity
- Perform vendor onboarding checks with defined risk criteria.
- Integrate continuous monitoring systems.
- Create repeatable workflows for audits and reassessments.
- Establish incident response playbooks that include vendor breaches.
- Leverage cybersecurity experts or TPRM service providers.
Why Partner with a TPRM Expert?

As third-party risks increase, in-house security teams are often stretched thin. Engaging with a specialized TPRM partner gives you:
- Scalable and repeatable vendor evaluation workflows.
- Deeper visibility into digital supply chain threats.
- Access to tested tools and methodologies.
Managing Third-Party Risks in Cybersecurity
In today’s digital-first environment, businesses must be proactive about cybersecurity. As reliance on vendors grows, so do the potential security and compliance risks. Third-party data breaches can have severe financial, reputational, and operational consequences.
Specialized TPRM firms provide expert guidance, tools, and scalable solutions that help companies maintain a strong security posture.
Managing third-party risks isn’t just a compliance exercise—it’s a business necessity. Cyber Defense Group can help you build a robust third-party risk management strategy that aligns with your business objectives and minimizes exposure.
Get in touch to learn how Cyber Defense Group can help secure your digital supply chain.
Q: What is third-party risk management?
A: Third-party risk management (TPRM) is the process of identifying and mitigating cybersecurity and compliance risks introduced by external vendors and suppliers.
Q: Why is third-party risk management important?
A: TPRM protects your organization from data breaches, compliance failures, and operational disruptions caused by third-party vulnerabilities.
Q: How often should third-party risk assessments be conducted?
A: Most organizations perform them annually or when onboarding new vendors, but continuous monitoring is ideal for high-risk environments.
