Under Attack? Contact Us
Results-driven approach to cybersecurity.
Every business is unique, your security program
should be as well.
Every 39 seconds, a cybersecurity attack occurs. In the event of a data breach, the consequences can be severe, including financial losses, legal liabilities, reputational damage, or even a complete business shutdown. From ransomware and phishing attacks to IoT, cloud, machine learning, and AI attacks — not to mention software vulnerabilities — businesses face a wide range of cyberthreats that require proactive and effective information security measures to mitigate.
At Cyber Defense Group, our sweet spot is designing Cybersecurity as a Service to help you stay one step ahead of today’s increasingly complex cybersecurity landscape and keep your business safe as you scale and grow. Our full-service cybersecurity team will help you strengthen your security posture so your business can proactively monitor, prevent, identify, investigate and respond to cyberattacks, 24/7.





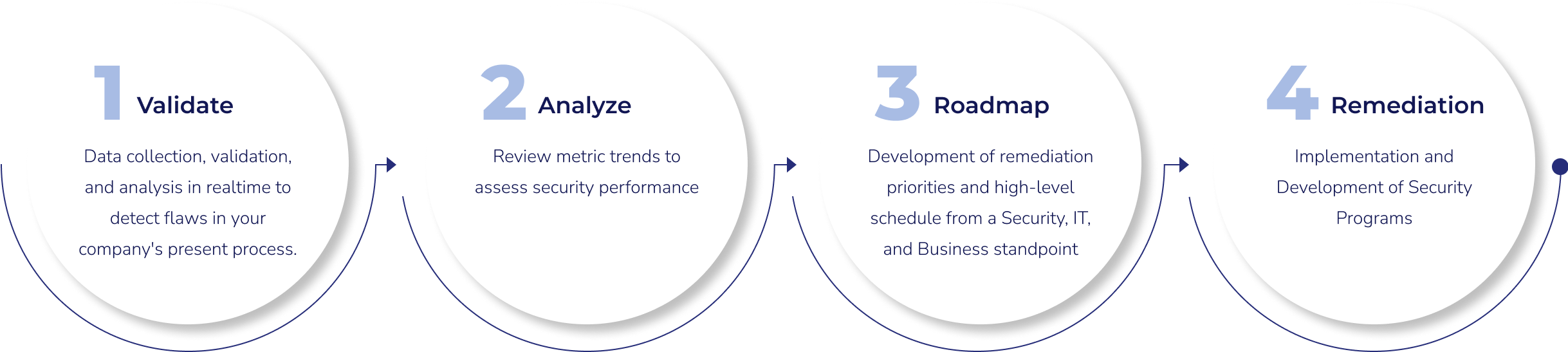
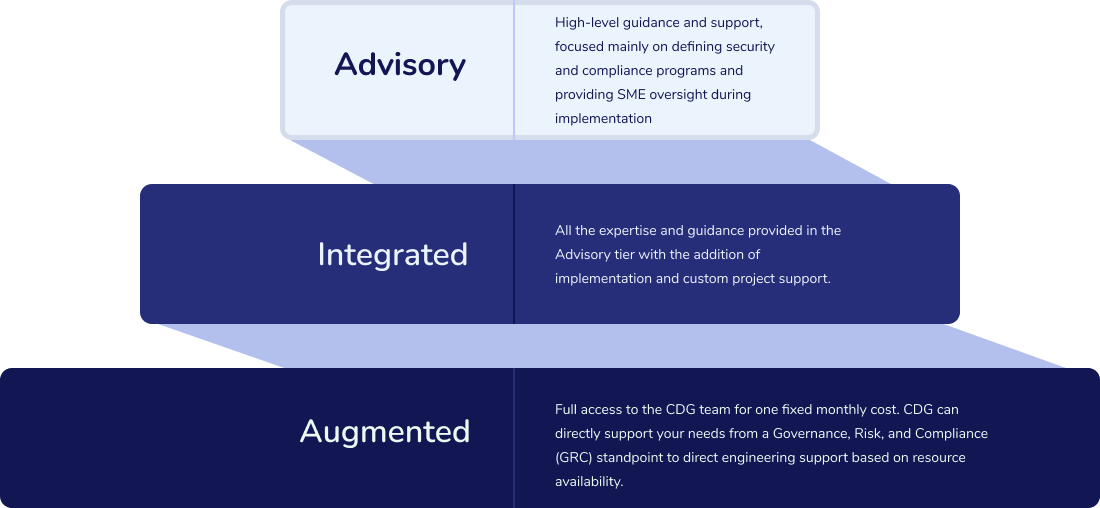
Cybersecurity as a service is broken down into three tiers – Advisory, Integrated, and Augmented. In all these tiers, Cyber Defense Group aims to provide strategic and tactical solutions, reduced cyber risk by increasing security control maturity, compliance with all regulatory requirements, address ongoing questions and issues around cybersecurity, and visibility to the board, C-suite, and other stakeholders around the risks, threats, and security maturity of the organization.

Copyright © 2024 CDG. All Rights Reserved