Under Attack? Contact Us
Get access to our cybersecurity knowledge repository. Prepare your defense against cyber threats with comprehensive guides and research.

March 6, 2024
Reading Time: < 1 minute

March 1, 2024
Reading Time: < 1 minute
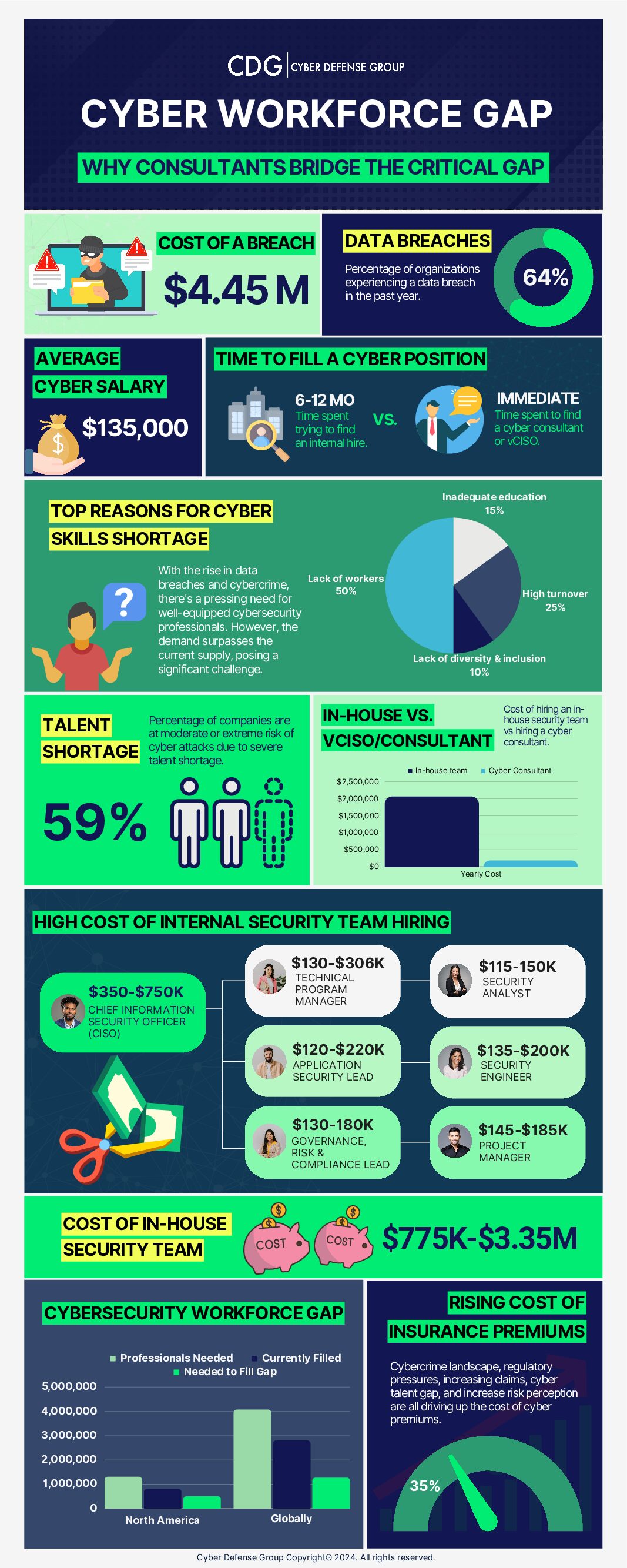
Infographic: Explore the cybersecurity talent gap and discover why a cybersecurity consultant could be the solution. This engaging visual presents key insights and industry trends effectively.

February 15, 2024
Reading Time: < 1 minute


Reading Time: < 1 minute


February 2, 2024
Reading Time: < 1 minute

Interactive worksheet to help you understand how and what to allocate to your security budget.

Building a robust and effective cybersecurity spending budget can be a daunting task.

January 19, 2024
Reading Time: < 1 minute

January 9, 2024
Reading Time: < 1 minute

December 11, 2023
Reading Time: < 1 minute


October 2, 2023
Reading Time: < 1 minute

September 25, 2023
Reading Time: < 1 minute


September 6, 2023
Reading Time: < 1 minute

August 29, 2023
Reading Time: < 1 minute

August 28, 2023
Reading Time: < 1 minute

August 2, 2023
Reading Time: < 1 minute
February 15, 2023
Reading Time: < 1 minute

November 28, 2022
Reading Time: < 1 minute


September 30, 2022
Reading Time: < 1 minute

September 15, 2022
Reading Time: < 1 minute




Reading Time: < 1 minute


Reading Time: < 1 minute

July 31, 2022
Reading Time: < 1 minute
Reading Time: < 1 minute

July 30, 2022
Reading Time: < 1 minute

July 21, 2022
Reading Time: < 1 minute

Reading Time: < 1 minute




March 17, 2022
Reading Time: < 1 minute

March 8, 2022
Reading Time: < 1 minute


September 28, 2021
Reading Time: < 1 minute

September 14, 2021
Reading Time: < 1 minute

March 24, 2021
Reading Time: < 1 minute

January 15, 2021
Reading Time: < 1 minute

January 7, 2021
Reading Time: < 1 minute

December 4, 2020
Reading Time: < 1 minute

August 11, 2020
Reading Time: < 1 minute


May 19, 2020
Reading Time: < 1 minute

April 28, 2020
Reading Time: < 1 minute

April 14, 2020
Reading Time: < 1 minute

Copyright © 2024 CDG. All Rights Reserved