Under Attack? Contact Us
Our mission is steadfast: to forge a more secure future for mid-market businesses. In an era of relentless digital transformation, we are committed to ensuring that companies like yours can boldly pursue innovation and growth, backed by our comprehensive and advanced security services. At Cyber Defense Group, your protection is not just our priority—it’s our passion. We dedicate ourselves to delivering cybersecurity solutions that are as dynamic and forward-thinking as the businesses we serve.

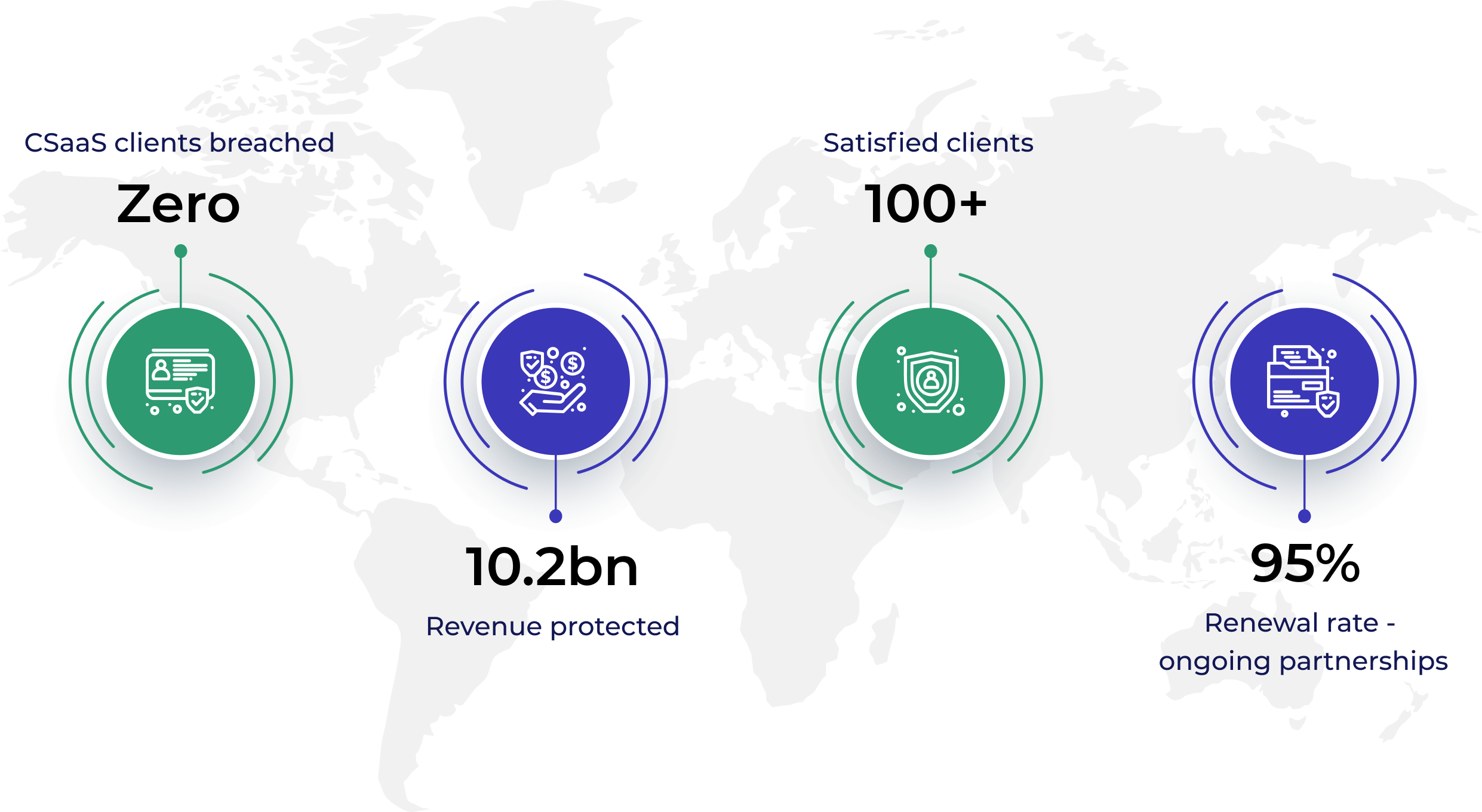

Cyber Defense Group specializes in delivering comprehensive cybersecurity consulting solutions tailored for small and medium-sized enterprise (SME) companies across all sectors. These organizations, grappling with the complexities of cloud infrastructure and lacking in-house cybersecurity expertise, face unique challenges such as resource constraints, evolving cyber threats, and regulatory compliance pressures. Cyber Defense Group meets these needs with robust, strategic, and flexible cybersecurity solutions, finely tuned to each client’s specific business objectives and risk profiles.

Identify vulnerabilities and risks in your organization’s systems or data security. Take steps for remediation, including recommendations for risk mitigation. Strengthen defenses and enhance overall cybersecurity posture through proactive detection and mitigation of security gaps.

Protect your most sensitive data with our managed cybersecurity services. We provide essential tools and processes to ensure security against cyberattacks. Harness the expertise and resources of our dedicated professionals from diverse industries, at a cost lower than hiring a full-time employee.

Respond promptly to cybersecurity incidents with rapid response and recovery, detecting, assessing, and containing threats. Mitigate damages, protect data, and strengthen overall security through technical measures, compliance, communication strategies, and post-incident analysis.















Copyright © 2024 CDG. All Rights Reserved